Recently while reverse engineering a piece of malicious macOS software to study what exactly it does, I noticed something odd in the binary. There seemed to be a little signature or message in the binary.
(c) 2014 - Cryptic Apps SARL - Disassembling not allowed
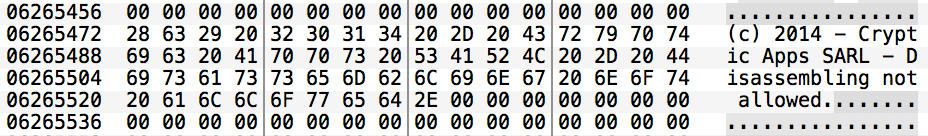
String in hex dump
It didn’t look like something the author would have added to “sign their work” so I decided to look into it a bit. My first guess might have been that this executable was packed with some obfuscation product, but this particular binary didn’t appear to be packed at all.
I tried punching the string into a web search, but nothing came up. I looked up “Cryptic Apps” and realized this is the maker of Hopper Disassembler, a cheaper alternative to IDA. One of the limitations to at-least the demo of Hopper is that it is not able to disassemble itself, so I tried opening the malicious binary in the Hopper demo to see what would happen.
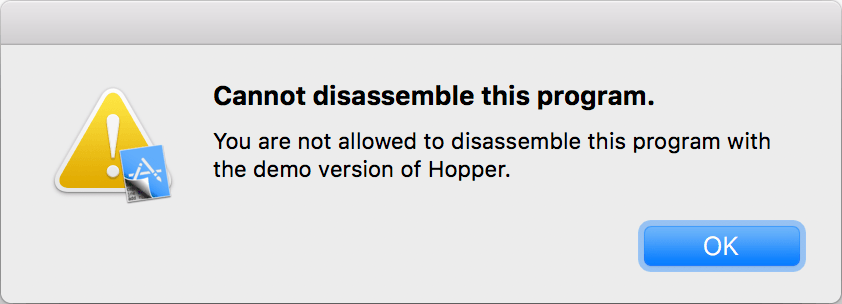
“Cannot disassemble the program.”
Yep, as it turns out this sequence of bytes is at-least one of the ways Hopper detects itself, and refuses to disassemble it.
It seems the author of this binary reverse engineered Hopper’s detection signature, which probably wasn’t very hard given how obvious it is, in order to exploit the DRM in Hopper to try to stop novice hackers from analyzing their code.
Cheap trick.
Bypassing the trick is obviously as simple as overwrite this string before disassembling. Of course, you could also use literally any other disassembler without issue.
Comments